Penetration Testing Service
Our Penetration Testing Service goes beyond standard security checks. We simulate real-world cyberattacks to identify weaknesses in your digital defenses, ensuring your systems are fortified against threats. Stay secure, stay confident.
Get a Free QuoteWhy Choose Our Penetration Testing Service?
Identify Weaknesses
Gain a comprehensive understanding of your digital vulnerabilities. Our meticulous assessment uncovers hidden weaknesses, ensuring a thorough examination of your systems, applications, and networks.
Prevent Breaches
Stay one step ahead of cyber threats by addressing vulnerabilities before malicious actors can exploit them. Our proactive approach prevents potential breaches, safeguarding your sensitive data and business operations.
Expert Analysis
Trust in the expertise of our certified penetration testers. With a proven track record in the field, our ethical hackers bring years of experience to every assessment, ensuring a comprehensive evaluation of your digital infrastructure.
Custom Solutions
Recognizing that every organization's cybersecurity needs are unique, we tailor our penetration testing strategies accordingly. Our approach is customized to match your specific environment, ensuring targeted assessments.
Actionable Insights
It's not just about identifying vulnerabilities; it's about taking meaningful action. Our detailed reports provide you with actionable insights, empowering your team to prioritize and address vulnerabilities effectively.

Work with us and join 3000+ satisfied customers!
Get a Free QuoteFrom Assessment to Security Enhancement:

Consultation
Understanding your objectives and requirements.
Our journey begins with understanding your unique cybersecurity needs. We collaborate closely to comprehend your objectives, system architecture, and potential areas of concern


Assessment
Our experts simulate real-world attacks.
Our certified penetration testers step into the shoes of a malicious actor. Using industry-leading methodologies, they simulate real-world attacks to identify vulnerabilities across your digital landscape.


Analysis
Identify vulnerabilities across your digital ecosystem.
Armed with an array of advanced tools and extensive experience, our engineers conduct a comprehensive analysis. They uncover weaknesses, potential entry points, and vulnerabilities that could expose your organization to cyber threats.


Reporting
Receive detailed reports with prioritized action items.
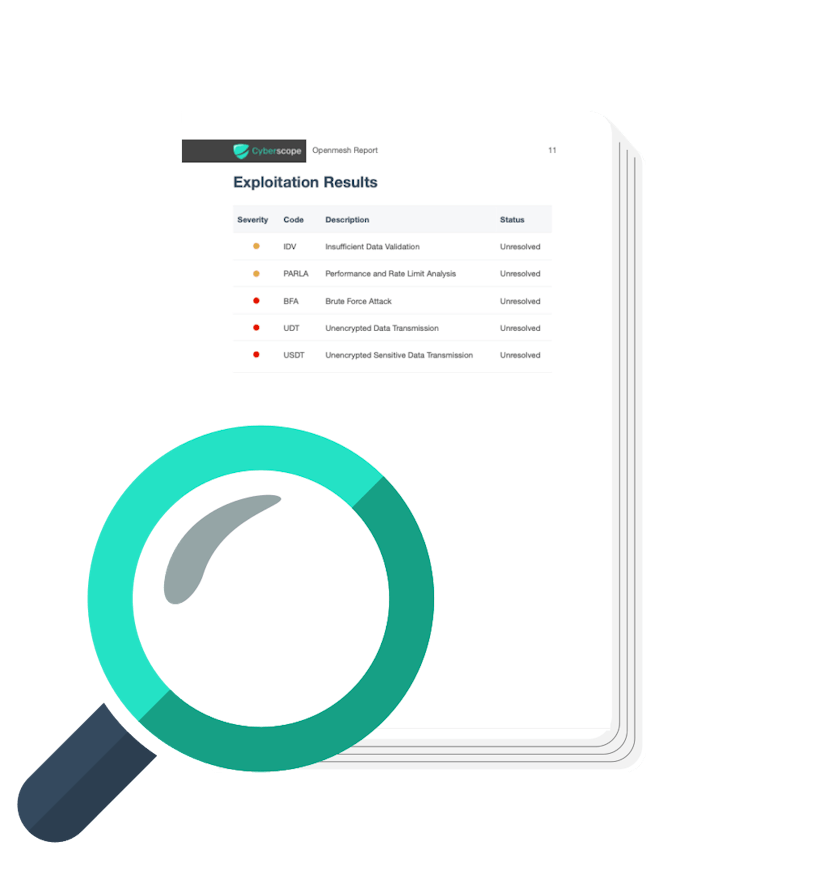
We believe in actionable insights. Our detailed reports provide a comprehensive overview of the vulnerabilities discovered, their potential impact, and actionable recommendations for mitigation.


Mitigation
Take targeted steps to enhance your cybersecurity.
With our reports, your team can take immediate steps to enhance your cybersecurity posture. With prioritized action items, you can confidently address vulnerabilities, secure your digital assets, and prevent potential breaches.
Notable Features
Comprehensive Testing:
Covering applications, networks, and systems.
Ethical Hackers:
Certified penetration testers with proven track records.
Custom Approaches:
Tailored strategies to match your specific needs.
Regulatory Compliance:
Ensuring adherence to industry standards.
Timely Reporting:
Receive detailed insights to act promptly.
Common Questions
What is penetration testing and why is it important?
Penetration testing is a simulated cyber attack conducted by ethical hackers to identify vulnerabilities in your digital infrastructure. It's crucial because it helps you proactively discover weak points before malicious actors exploit them, enhancing your overall cybersecurity.
How do you ensure the confidentiality of our data?
Data security is paramount. We follow strict confidentiality protocols, and our engineers adhere to stringent ethical guidelines. Your data is handled with the utmost care and only shared with authorized personnel involved in the assessment.
How do I interpret the results of the penetration test?
Our detailed reports are designed to be easily understood by both technical and non-technical stakeholders. We provide clear explanations of vulnerabilities, their potential impact, and recommended actions for mitigation.
What happens after vulnerabilities are identified?
Our partnership doesn't end with identification. We provide you with actionable insights and prioritize vulnerabilities based on their severity. Your team can then take targeted steps to address vulnerabilities and enhance your cybersecurity.
Is penetration testing a one-time effort?
Cyber threats are constantly evolving, and so is our approach. While one-time penetration testing is valuable, regular assessments are recommended to ensure ongoing protection against emerging threats and to keep your defenses up to date.
How often should I conduct penetration testing?
The frequency of penetration testing depends on various factors such as industry regulations, system changes, and threat landscape shifts. Regular testing, such as quarterly or annually, ensures you stay ahead of evolving threats.